About the observatory
Our Methodology
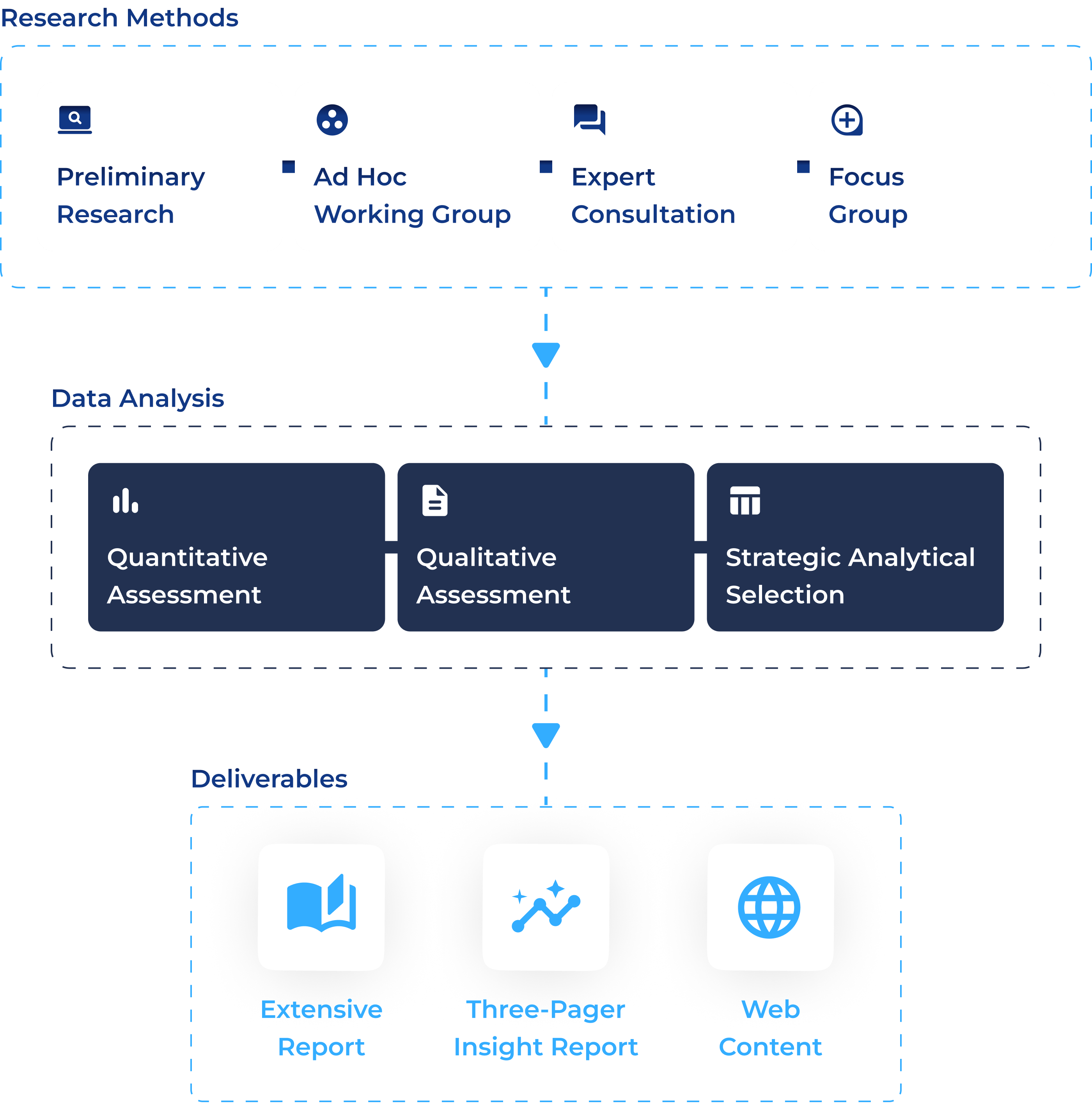
To help your decision making with easy to understand data about emerging cyber threats and market intelligence.The activities of the NC3 observatory are meant to provide evidence about the main and emerging characteristics of the cybersecurity needs related to the national ecosystem. Evidence is derived from a systematic and rigorous process of observation, data collection, analysis, and interpretation. Since NC3 aims to support the national ecosystem, this process is crucial for establishing the validity and reliability of published information. An overview of our NC3 approach and methodology based on observations can be summarised as:
Enquiries and investigations begin with observations of cybersecurity phenomena or the formulation of specific research questions.
Observations can be made through direct or indirect collection of domain information.
Once a phenomenon is observed or a question is posed, cybersecurity experts interpret the the information and formulate hypotheses. A hypothesis is a testable, specific statement that proposes a potential explanation for the observed phenomenon.
Scientists design experiments or observational studies to collect relevant data and test the hypotheses.
The experimental design should include variables (independent and dependent), controls, and a clear procedure for data collection.
Data is collected through controlled source of information , field observations, surveys, or other appropriate methods.
Data can be qualitative (descriptive) or quantitative (numerical), depending on the research goals.
Collected data about cybersecurity and the related domain of interest is analyzed using statistical and analytical techniques. The choice of analysis depends on the nature of the data and the research question.
Statistical analysis helps identify patterns, relationships, and trends in the data.
Scientists interpret the results of their analyses in the context of the original hypothesis and draw conclusions and inferences about the observed cybersecurity phenomenon.
To ensure the reliability and validity of evidence, submit their findings for peer review. Experts in the field assess the study's methodology, results, and conclusions.
If the research passes peer review, it can be published in dedicated reports, magazine, journals or presented at conferences. Publication makes the findings accessible to the community.
Over time, as evidence accumulates and is validated by observation, it can contribute to the development or refinement and consolidation of the knowledge base to be shared with the users of the observatory.
The evolving characteristics of the cybersecurity domain are constantly changing, and knowledge must evolve in tandem. Acquired knowledge is therefore dynamically subject to continuous revision as new evidence emerges. Ongoing observations and research help refine existing knowledge and generate new questions for investigation.
This methodology of evidence based on observations forms the foundation of the method adopted by NC3. It is a systematic approach to understanding the continuous evolutions that characterise the cybersecurity domain. It ensures that knowledge is reliable, verifiable and available to the community in an open and transparent manner.
Our Metholodogy
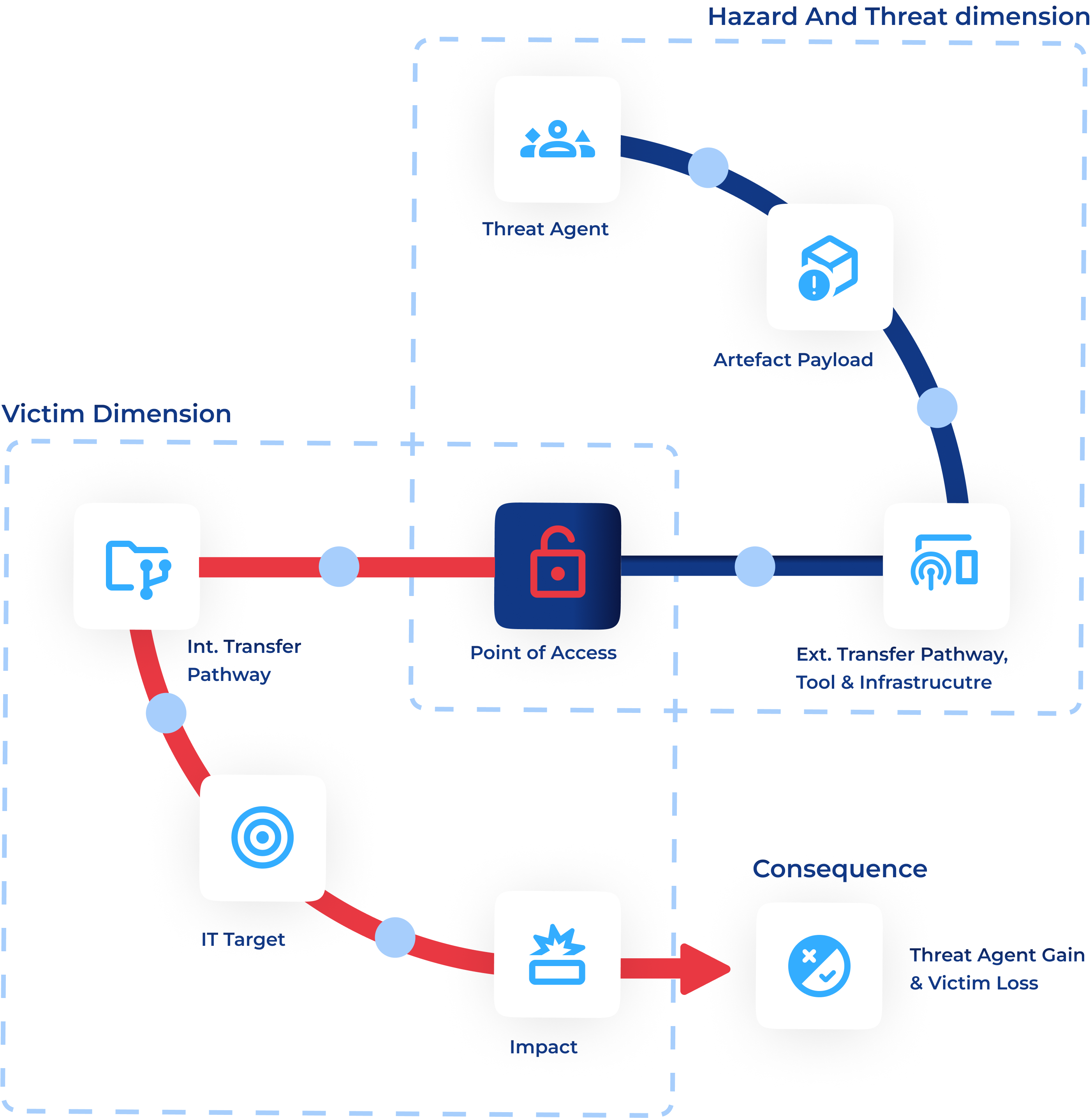
The bulletin is released quarterly and the reported information is structured according to the NC3 threat conceptual model. The information about emerging threats is described along the pathway described by the model, i.e., considering two main dimensions Learn more about our modelarrow_forward