Cybersecurity Threat Analysis
Every quarter, this section of the Observatory details and analyses emerging threats for a non-technical audience, structured using the NC3 threat conceptual model.
2022
General Overview for the the period
Get a rapid overview of the main cyber security incidents identified and attributed this quarter, along with a trend comparison to the previous quarter.
Q2 2024
Threat Landscape
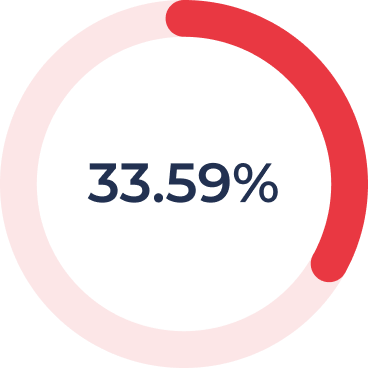
Main Threat Actor

APT28
14
arrow_upward10
Main External Pathways

Phishing
2539
arrow_upward335
Main Infrastructures

IoT
273
arrow_upward-73
Main Tools

FormBook
142
arrow_upward76
Main Access Points & Prevention
Main Access Point

CVE
956
arrow_upward614
Main Target & Impact
Main Target
Healthcare and public health
16
arrow_upward16
Main Impact
Ransom
101
arrow_upward64
Detailed View & Analysis
Dive deeper with a comprehensive breakdown of each cyber incident identified this quarter, including analyses, attribution evidence, and comparative metrics.
Q2 2024
Threat Agent Activities
Who were the main threat actors acting during the period?
Our analysis
In the second quarter of 2024, APT28, linked to Russia, significantly increased its operations with 14 attacks (250% increase from Q1). The North Korean Lazarus Group saw a reduction to 5 attacks (a 64.3% decrease from 14), while Turla maintained steady activity with 5 attacks in both quarters. Kimsuky, another North Korean group, reported a decrease to 3 attacks (an 80% drop from 15). MuddyWater and Gamaredon Group showed new or increased activities, with 3 and 2 attacks respectively. New entrants like APT-C-36, FIN7, Elephant Beetle, and Andariel also appeared in Q2.
Threat Actors Name
Attributed Events

Trend

APT28 is a threat group that has been attributed to Russia's General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS) military unit 26165.
Lazarus group is a North Korean state-sponsored cyber threat group; it uses a wide range of methods depending on the characteristics of the campaigns carried out and the objectives pursued. It mainly aimed at manipulating employees of strategically important companies such as those involved in the military or aerospace industry
Turla is a Russian-based threat group that has infected victims in over 45 countries, spanning a range of industries including government, embassies, military, education, research and pharmaceutical companies since 2004 is a cyber espionage group operating against targets in East Asia, particularly Taiwan, and occasionally, Japan and Hong Kong. Based on the mutexes and domain names, BlackTech's campaigns are likely designed to steal their target's technology.
Kimsuky is a North Korea-based cyber espionage group that has been active since at least 2012. The group initially focused on targeting South Korean government entities, think tanks, and individuals identified as experts in various fields, and expanded its operations to include the United States, Russia, Europe, and the UN. Kimsuky has focused its intelligence collection activities on foreign policy and national security issues related to the Korean peninsula, nuclear policy, and sanctions
No Description
ATP29 is a Russian hacker group believed to be associated with one or more intelligence agencies of Russia, it primarily targets Western governments and related organizations, such as government ministries and agencies, political think tanks, and governmental subcontractors.
Gamaredon Group has been active since at least 2013 and has targeted individuals likely involved in the Ukrainian government
External Transfer Pathways
Ways harmful files or content are sent from external sources.
Our analysis
In the second quarter of 2024, phishing incidents rose from 2204 to 2539, marking a 15.2% increase. Smishing attacks surged by 152.6%, increasing from 57 to 144. The number of attacks increased significantly, from 8 to 93, representing a 1062.5% rise. Execution-related incidents rose by 540%, from 10 to 64. Defense evasion emerged as a new category with 56 incidents, having none in Q1. Collection activities increased by 33.3%, from 21 to 28. DNS hijacking incidents rose from 4 to 22, a 450% increase. Malspam incidents saw a modest rise of 25%, from 12 to 15. On the other hand, DDoS attacks slightly decreased by 16.7%, from 6 to 5. These shifts highlight the evolving landscape of cyber threats, necessitating robust and adaptive cybersecurity measures.
Pathway
Attributed Events

Trend

Focus on Phishing

With the support of SpamBee we collected the main keywords and email addresses associated with phishing attacks

Phishing



0
arrow_upward0



Keywords & Email Addresses Identified:
Infrastructures
Infrastructures represent the systems used to help carry out attacks.
Our analysis
In the second quarter of 2024, the landscape of cyber-attack infrastructures shifted significantly. The total number of entries rose from 4567 in Q1 to 7290 in Q2. IoT infrastructure, despite seeing a reduction from 346 to 273 incidents, remained a major component. Botnet infrastructure incidents increased dramatically from 3 to 71, a significant rise. Command and Control (C2) infrastructures emerged prominently with 52 reported incidents, having had no activity in the previous quarter. DNS infrastructures also saw a notable increase, rising from 5 to 20 incidents.
Infrastructure
Attributed Events

Trend

Tools
Types of viruses used to exploit or damage digital systems.
Our analysis
In Q2 2024, notable increases in malware incidents were observed. FormBook incidents rose from 66 to 142, a 115.2% increase, driven by persistent phishing campaigns exploiting vulnerabilities through malicious email attachments. Remcos incidents grew from 83 to 141, a 69.9% rise, due to its remote access capabilities being leveraged in targeted attacks. NjRAT incidents doubled from 60 to 122, a 103.3% rise, attributed to its ease of deployment and extensive functionalities for remote control and data exfiltration. Lokibot saw a significant increase from 26 to 62 incidents (138.5%), driven by its data-stealing capabilities. Mirai incidents surged from 1 to 17, a 1600% increase, due to ongoing exploitation of IoT vulnerabilities for creating botnets used in large-scale DDoS attacks.
Tool
Attributed Events

Trend

Point of Access
Review the indentified gateways that have been used as entry points in previous cyber incidents.
Our analysis
Incidents involving Common Vulnerabilities and Exposures (CVE) saw a notable increase, surging from 342 to 956, a 179.5% increase. Vulnerability incidents rose from 20 to 104, representing a 420% rise, while zeroday incidents grew from 9 to 15, an increase of 66.7%. Server-related incidents jumped from 1 to 14, Dropbox incidents from 1 to 10, and Windows incidents from 1 to 8. Web browser-related incidents increased from 2 to 7, and Facebook-related incidents doubled from 1 to 2. Additionally, Citrix incidents, which had no activity in Q1, recorded 2 incidents in Q2.
Point of Access
Attributed Events

Trend

Component and System Vulnerabilities
Inspect known weak spots within software and hardware, complemented by details on available protective patches.
Component

Vulnerability

CVE Identifier

Protective Patch

Type of Impact
Various outcomes of cyber threats identified.
Our analysis
In the second quarter of 2024, ransomware incidents surged by 173%, rising from 37 to 101 incidents, largely due to exploited vulnerabilities and compromised credentials. Scam incidents increased by 154%, from 24 to 61, driven by the high prevalence of phishing categorized as scams. Espionage-related incidents also grew by 60%, from 5 to 8, reflecting heightened intelligence-gathering activities.
Type of Impact
Attributed Events

Trend

IT Target
Highlighting specific IT objectives that cyber attackers aimed for.
Our analysis
In the second quarter of 2024, incidents targeting various IT systems showed notable changes. The total number of entries rose from 4567 in Q1 to 7290 in Q2. Attacks on Windows systems saw a significant increase, jumping from 1 incident in Q1 to 16 in Q2, representing a dramatic rise. Credential-related incidents also surged, from 1 to 13. Exchange server incidents remained constant at 1, while attacks targeting Office 365 dropped from 1 to 0.
Type of Impact
Attributed Events

Trend

Type of Victim
Diverse sectors targeted by cyber threats during the period.
Our analysis
In the second quarter of 2024, cyber incidents affecting various sectors displayed notable trends. Incidents targeting healthcare and public health surged from 0 to 16. However, defense sector incidents declined from 16 to 9. Financial services incidents increased from 1 to 9, while government facilities saw a rise from 2 to 8. Manufacturing and education facilities each reported 3 incidents, up from none in the previous quarter.
Infrastructure
Attributed Events

Trend